- Ashish Batwara
Your sales team just closed a deal. Great news. Then the customer asks: “Do you integrate with CrowdStrike?”
You check the roadmap. CrowdStrike is not on it. But the customer needs it for their SOC 2 audit, and the deal is worth $50K in ACV. So you pull two engineers off the roadmap and tell them to build it.
Six weeks later, the integration ships. The customer is happy. But now another prospect wants SentinelOne. And another wants Microsoft Defender. And your integration backlog is growing faster than your team can clear it.
Sound familiar?
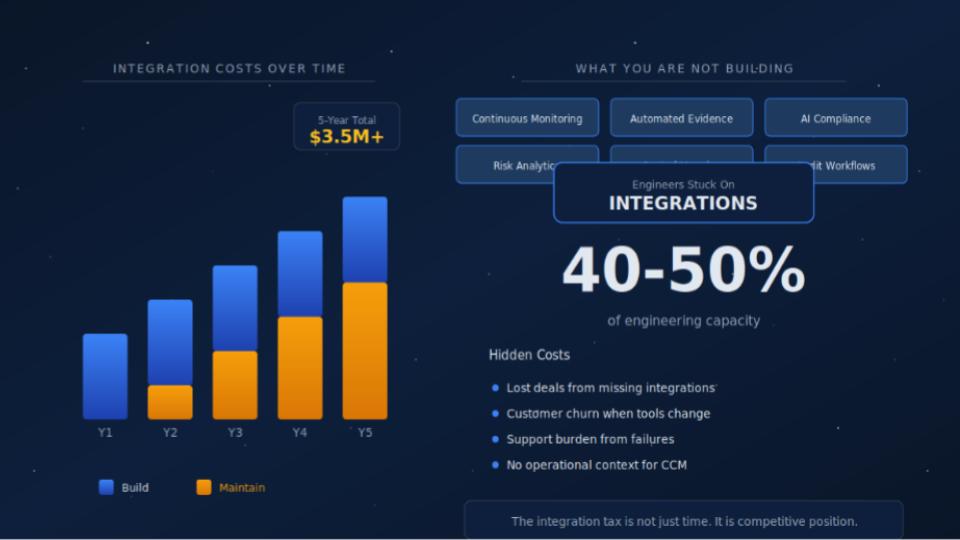
This is the integration tax. And most GRC platforms underestimate how much it actually costs.
The Real Math on Building Integrations
Let us say your platform needs to support 40 security tools to be competitive. That is a reasonable number. Your customers use different combinations of EDR, identity, vulnerability scanners, cloud security tools, and ticketing systems. They expect you to pull data from all of them.
Here is what that actually costs:
Initial Build
Support 20 vendors across a full engineering team (dev, QA, DevOps, infra): 12+ months minimum. You are looking at a team of 4+ engineers working on nothing but integrations.
That is not just connecting to an API. It is handling authentication, pagination, rate limiting, error handling, retries, data normalization, and testing. At $200K fully loaded cost per engineer, you are talking over a million dollars just to build them.
Ongoing Maintenance
But building is just the beginning. Vendor APIs change. CrowdStrike releases a new version. Okta deprecates an endpoint. AWS updates their authentication flow. Each integration needs about 80 hours of maintenance per year, plus another 40 hours when breaking changes hit. That is 4,800 hours annually, which works out to about 2.3 full-time engineers doing nothing but keeping existing integrations running.
At $200K per engineer, that is $460K per year just for maintenance. Every year. Forever. The absolute cost grows into millions of dollars annually, recurring indefinitely.
The 5-Year Picture
Add it up over five years: over $1M to build plus $2.3M in maintenance equals $3.5 million. That is $88,000 per integration over five years. For what is essentially plumbing.
The Hidden Costs Nobody Budgets For
The numbers above are just the direct engineering costs. They do not include:
Opportunity Cost
Every engineer building integrations is an engineer not building product features. Those 2.3 FTEs maintaining integrations could be shipping features that differentiate your platform. Instead, they are debugging why the Tenable API started returning 429 errors.
Early-stage teams lose 40-50% of their engineering capacity to integration work. Scaled teams look more efficient by percentage, but they are still spending millions annually on integration maintenance. That is engineering capacity that could be building the “smart” compliance features that actually beat your competition.
Lost Deals
How many deals have you lost because you did not have a specific integration? If you lose just four deals per year at $50K ACV because you could not support their security stack, that is $200K in lost revenue. And that is probably a conservative estimate.
Customer Churn
Customers do not always tell you why they leave. But when they outgrow your integration coverage, or when your integration breaks during their audit prep, they start looking at competitors who have better coverage.
Support Burden
Every integration generates support tickets. Authentication issues. Sync failures. Data discrepancies. Your support team becomes an extension of your engineering team, and neither team is happy about it.
No Operational Context
Here is the cost nobody talks about: when you are drowning in integration maintenance, you cannot build operational context. Operational context is a shared, consistent understanding of what is actually true across your customer’s security environment. Without it, your platform is just aggregating data. With it, you can deliver Continuous Control Monitoring that actually works.
You cannot build operational context if your engineering team is spending all their time on plumbing.
The "Just One More" Trap
The most dangerous phrase in integration planning is “just one more.”
Sales closes a big deal, and the customer needs Wiz. It is just one more integration. How hard could it be? So you build it. Then another customer needs Lacework. And another needs Prisma Cloud. Each one is “just one more,” but the maintenance burden compounds.
Here is the thing: your customers do not use “just one more” tool. They use dozens. The average enterprise security stack has 40+ tools. And they expect your platform to work with all of them.
You cannot build your way out of this. Every integration you add increases your maintenance burden. And you will never catch up to customer demand because the security tool market keeps expanding.
The Build vs. Buy Decision
At some point, every engineering leader faces this question: should we keep building integrations in-house, or should we embed a solution?
Here is a simple framework:
Build in-house if:
Integrations are your core product differentiator. You only need a handful of integrations (fewer than 5). You have dedicated integration engineers with nothing else to do. You enjoy debugging vendor API changes at 2am.
Consider a signal fabric if:
You need broad coverage across security categories. Your engineers should be building product, not plumbing. Customers keep asking for “just one more” integration. You would rather not maintain 40+ vendor API connections forever. You want to deliver Continuous Control Monitoring, not periodic batch pulls.
What Embedding Signal Infrastructure Looks Like
When we talk about embedding a solution, we do not mean hiring consultants to build integrations for you. That just shifts the cost without solving the maintenance problem.
We mean embedding signal infrastructure into your platform. Your customers authenticate their security tools through a UI you embed. You call a single API to get Normalized Evidence Signals, not raw vendor logs. When CrowdStrike changes their API, someone else handles the update.
You get real-time evidence streams through the Webhook Exchange, not periodic batch pulls. Your AI features work because the data is already normalized. And you can actually focus on building the compliance logic that wins your market.
The math changes dramatically. Instead of 4+ engineers for 12+ months, you integrate in weeks. Instead of 2.3 engineers maintaining vendor connections, you maintain one SDK and almost zero maintenance cost. Instead of $3.5M over five years, you are looking at a fraction of that.
Quantify Your Integration Tax
Every GRC platform’s situation is different. The number of integrations you need, your engineering costs, your vendor mix. But the pattern is the same: building integrations in-house costs more than most teams realize, and the maintenance burden compounds over time.
We built a calculator to help you quantify your specific integration tax. Plug in your numbers and see what you are actually spending. Even if you decide to keep building in-house, at least you will know the true cost.
Calculate your integration cost: https://unizo.ai/diy-integration-cost-calculator/
—
Related Reading:
For more on the integration tax and how to solve it, see “The Integration Tax: What It’s Really Costing You” on unizo.ai, part of our series on building AI-ready security infrastructure.